In today's digital age, organizations often depend on collaborative tools like Azure Wiki to streamline knowledge sharing among team members. However, there are situations when you might need to export this content for further analysis, archival purposes, or integration with other systems.
In this article, we'll see how to import Azure Wiki content into a JSON file using Azure DevOps Services REST API with Python.
Prerequisites
Here you need:
Before we dive into the implementation, ensure you have the following as well:
- Azure DevOps Account: Make sure you have access to an Azure DevOps account with permission to read wiki content. You can create an Azure free account via Azure Free Account.
- Personal Access Token (PAT): Generate a PAT in your Azure DevOps account with appropriate permissions to access the wiki content via the REST API. To create a PAT, log in to your DevOps portal and navigate to the Personal Access Token section.
From there, define the period for the token activation and level of permissions. Once done, it will create a token to use in your script.
Implementation
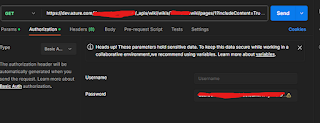
Step 1: Add the Script in POSTMAN
https://dev.azure.com/{organization}/{project}/_apis/wiki/wikis/{wikiIdentifier}/pages/1?includeContent=True&api-version=7.1-preview.1
When you add the above script, set the following parameters:
- Set the method as GET.
- Set the authorization to basic authentication, leave the username blank, and include the PAT token.
Click "Send" to see your Wiki content in the results.
Step 2: Create the Python Script
After a successful response from POSTMAN, use the following Python script to generate a JSON file:
import requests
import json
import base64
# Azure DevOps credentials and parameters
organization = '{organization}'
project = '{project}'
wiki_identifier = '{wikiIdentifier}'
api_version = '7.1-preview.1'
pat = 'PAT token'
username = "dummy"
combined_pat_token = username + ":" + pat
# API endpoint
url = f'https://dev.azure.com/{organization}/{project}/_apis/wiki/wikis/{wiki_identifier}/pages/1?includeContent=True&api-version={api_version}'
# Request headers with authorization
headers = {
'Authorization': 'Basic ' + base64.b64encode(combined_pat_token.encode('utf-8')).decode('utf-8'),
'Content-Type': 'application/json'
}
# Send GET request to Azure DevOps Wiki API
response = requests.get(url, headers=headers)
# Check if request was successful
if response.status_code == 200:
# Parse JSON response
wiki_content = response.json()
content_value = wiki_content.get('content')
if content_value:
# Save content value to a file
with open('wiki_content.txt', 'w') as file:
file.write(content_value)
print("Content value saved to 'wiki_content.txt'")
else:
print("Error: No content found in the response.")
else:
print(f"Error: Failed to retrieve Wiki content. Status code: {response.status_code}")
print(f"Response body: {response.text}")
Note: The username is set to "dummy" to avoid authentication errors. Let me know if you have a better way to handle this!
Conclusion
Let me know if you have any doubts or better ways to approach this task.